Introduction to hardening
This section is important if you use the Pimped Apache Status as monitor for productive systems in a larger network or it has public access from the internet. Or just for those who keep an eye to several security aspects.
Restrict access to server status pages
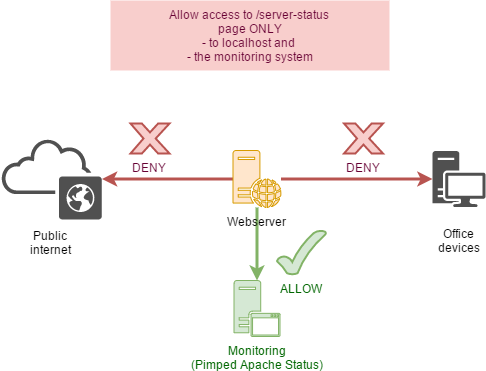
You never should not open the server status page
of the apache httpd to the internet.
Restrict the access to these IPs only, that should have access
to it: your monitoring system and maybe additional to workstations of the
administrators.
Deny the access to the server status pages to any other client.
IP restriction for /server-status
Important: This restriction must be repeated in the
settings on each webserver. If you use a Puppet/ Chef/ ... put this info
to a template.
Use apache possibilities with ALLOW, DENY rules for ip restriction (this is Apache 2.2 syntax; for Apache 2.4 see the docs).
<Location /server-status>
SetHandler server-status
Require ip 127.0.0.1
Require ip 192.168.100.101 # ip monitoring server
deny from all
</Location>
Apache 2.2 docs - access
Apache 2.4 docs - access
Secure access to monitoring data
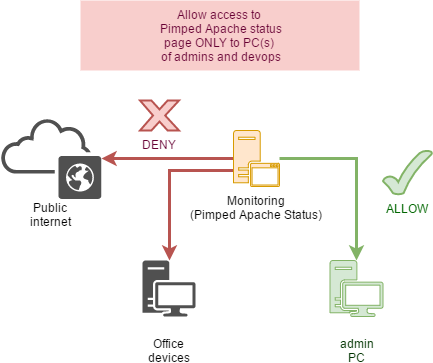
IP restriction
Use apache possibilities with ALLOW, DENY rules for ip restriction (this is Apache 2.2 syntax; for Apache 2.4 see the docs).
<Location /apachestatus>
order deny, allow
Require ip 192.168.123.101 # ip of admin pc 1
Require ip 192.168.123.102 # ip of admin pc 2
deny from all
</Location>
Apache 2.2 docs - access
Apache 2.4 docs - access
Password protection
The password protection is an additional access limitation.
You should use a password protection the access to the monitoring data.
(1)
Use internal user + password protection as simple variant. It allows only one, just a single user.
see section auth
Customization -> Custom Configuration
OR
(2)
use apache possibilities to configure passord based access for several users.
The most simple way is the method by htpasswd ... but it can be done based on a database or ldap
too.
Apache 2.2 docs - auth
Apache 2.4 docs - auth
SSL
Install an SSL certificate on the monitoring server if you use any of the password protection methods above. Otherwise user and password will be sent as clear text over the network.
Harden installation directory
File Permissions
For automatic installations with puppet or chef you can harden the application directory.
- all files must be readable by your apache user (apache or wwwrun or www-data).
- all files in the application folder should be writable for the apache user. Then you can update the software with your webbrowser.
minimal: only the subdirectories ./config/ and ./tmp/ (*) must be writable for the apache user.
(*) see next chapter
protect tmp directory
use folder outside approot
The tmp directory can be redefined with the "tmpdir" value. Set a complete path or false
to put the temp directory outside the webapp folder.
Customization -> Setup -> Configuration
deny access
If you leave the temp directory in the approot folder and you do not
allow to parse .htaccess then add the deny rule of tmp/.htaccess
in your apache vhost.
# ---------------------------------------------------------------------------
# DENY HTTP ACCESS
# ---------------------------------------------------------------------------
# Apache 2.4
<IfModule mod_authz_core.c>
Require all denied
</IfModule>
# Apache 2.2
<IfModule !mod_authz_core.c>
Order Allow,Deny
Deny from all
</IfModule>